After decades of miscues and rival countries stealing U.S. military intelligence, the federal government effectively drew a line in the sand. The development of the Cybersecurity Maturity Model Certification (CMMC) was to be the single standard that all military contractors and supply chain businesses followed. Previously CMMC 1.0 was the required certification version until CMMC 2.0 was recently announced and released.
But changes in the Pentagon and White House resulted in revisions of the initial CMMC standards and delayed implementation. To say this has also created confusion among organizations in the military-industrial base would be something of an understatement. Proactive industry leaders were quick to have their cybersecurity defenses assessed and updated to meet what seemed like an imminent CMMC 1.0 mandate. As the rollout date for CMMC 2.0 nears, decision-makers are trying to come to grips with the differences between CMMC 1.0, and 2.0, to maintain their lucrative Department of Defense (DoD) contracts.
Why DoD Requires CMMC 2.0
To understand CMC 2.0, it’s essential to know why the federal government decided to bring wide-reaching cybersecurity regulations under one umbrella. Before the CMMC initiative, contractors and peripheral businesses were largely given the latitude to self-assess their cybersecurity compliance.
Needless to say, not everyone maintained an adequate defensive posture, and hackers funded by America’s enemies breached systems and routinely pilfered off Controlled Unclassified Information (CUI). This data could be found in contracts, invoices, and electronic messages between outfits in the supply chain. Advanced persistent threats — working for countries such as Russia, Iran, and China — would piece CUI together to learn about our confidential national security defenses.
“A determined adversary with the right capabilities is going to find their way in, especially if they put all their resources to bear on it. So, it really comes down to, have you done everything you possibly can, have you been truthful about it,” Karlton Johnson, chair of the CMMC Accreditation Body board of directors, reportedly said. “One of the reasons we are doing CMMC is, people were not being truthful about it. If we go in and find out that you were not doing something, that’s negligence and we have to go that route.”
Back then, the federal government would fine or suspend negligent companies. As if adding insult to these injuries, foreign spies infiltrated the Solar Winds software used at almost every level of government as CMMC 1.0 was nearing its final stages. It was a cybersecurity and national defense nightmare.
How Does CMMC 2.0 Work?
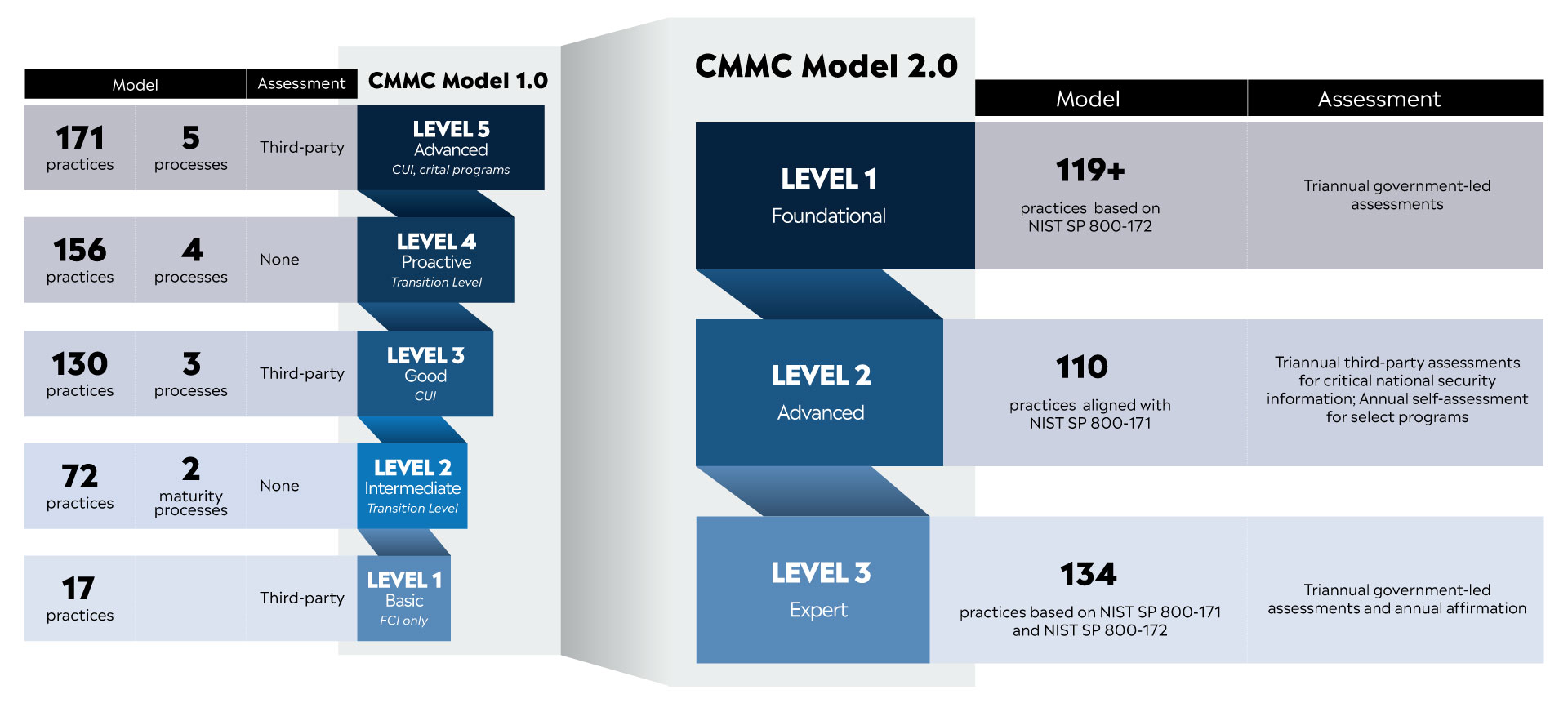
CMMC sets a singular, unified standard that more than 300,000 organizations in the military-industrial base must follow. The CMMC 2.0 guidelines involve a three-tiered system that set cybersecurity controls for companies that fall into a particular category.
The DoD refers to the three groups as Foundational, Advanced, and Expert levels. Each adopts defensive strategies from existing policies such as NIST SP 800-171 and NIST SP 800-172 subsets, among others. It’s not necessarily important for business professionals to know the ins and outs of NIST or even CMMC 2.0 for that matter. But it’s crucial to have a cybersecurity firm with CMMC expertise test, assess, and update your network to meet the incoming mandate. Failing to gain certification or maintain a robust posture could result in your company getting sidelined.
What are the Key Differences Between CMMC 2.0 and 1.0?
The glaring difference between the two measures is that CMMC 1.0 was going to be rolled out with five levels. The 2.0 version reduces that number to three. Although the latest version has fewer tiers, it remains equally complex for people outside the managed IT cybersecurity niche to fully appreciate. That being said, these are the CMMC 1.0 and 2.0 levels, respectively.
CMMC 1.0 Levels
- Level 1: Basic Cyber Hygiene that involves using most current antivirus software, firewalls, and a company-wide cybersecurity policy in place.
- Level 2: Intermediate Cyber Hygiene that involves implementing NIST standards to protect CUI.
- Level 3: Good Cyber Hygiene required 72 practices to be in place to earn certification. Organizations must also create a plan that demonstrates best practices and training.
- Level 4: Proactive Cyber Hygiene typically applies to military contractors who previously followed DFARS protocols, among others. The organization must demonstrate it can identify and repel advanced persistent threats.
- Level 5: Advanced Cyber Hygiene primarily for direct DoD contractors that requires sophisticated methods for identifying and responding to advanced persistent threats in real-time.
One of the challenges business professionals faced was determining which level applied to their company and meet that standard. Although CMMC 2.0 streamlines the tiers, it creates some confusion about certification methods.
CMMC 2.0 Levels
- Foundation: Loosely considered the equivalent of CMMC 1.0 Level 1, businesses must adhere to 15 controls to safeguard contractor information.
- Advanced: Organizations that store or transmit CUI must adhere to 110 controls to protect CUI. This level has been a pain point for companies because it involves different ways to maintain certification.
- Expert: Consistent with Level 5 of CMMC 1.0, companies must be able to detect, repel, and respond to advanced persistent threats. The controls in the Advanced tier rank among the most stringent 134 cybersecurity measures.
Going forward, companies working in the military-industrial base will be required to maintain CMMC 2.0 standards and demonstrate that to the federal government. The DoD is no longer interested in doling out fines after the fact. Advanced proof of CMMC 2.0 is now the standard.
Contact Sedulous Consulting Services For CMMC 2.0 Compliance
Based in Triangle, Virginia, Sedulous Consulting Services ranks among the first 100 organizations to qualify as a Third-party Assessment Organization. We work diligently with small and mid-sized businesses to assess their cybersecurity vulnerabilities, secure their network defenses, and meet the stringent CMMC 2.0 requirements. If your company enjoys profits from a military contract or works in the supply chain, contact Sedulous Consulting Services.