The mandatory implementation of cybersecurity regulations is quickly approaching for contractors in the defense industrial base.
As the Pentagon rolls out the second version of Cybersecurity Maturity Model Certification, aka CMMC 2.0 changes, interim rules are expected to go online. As a result, companies can anticipate seeing CMMC 2.0 language appear in the U.S. Department of Defense (DoD) and other lucrative contracts brokered by the federal government. The first interim rules are set for March 2023, meaning CMMC 2.0 mandates will likely appear in agreements come July 2023.
The idea that CMMC 2.0 rules won’t impact deals until July may not create a sense of urgency. But the time it takes to conduct a comprehensive cybersecurity analysis of systems, employee practices, and the way sensitive data is stored and transmitted could take months. Moreover, given the impact the following changes could have on contractors, business leaders could get sidelined if they procrastinate.
1: More Stringent Policies and Procedures
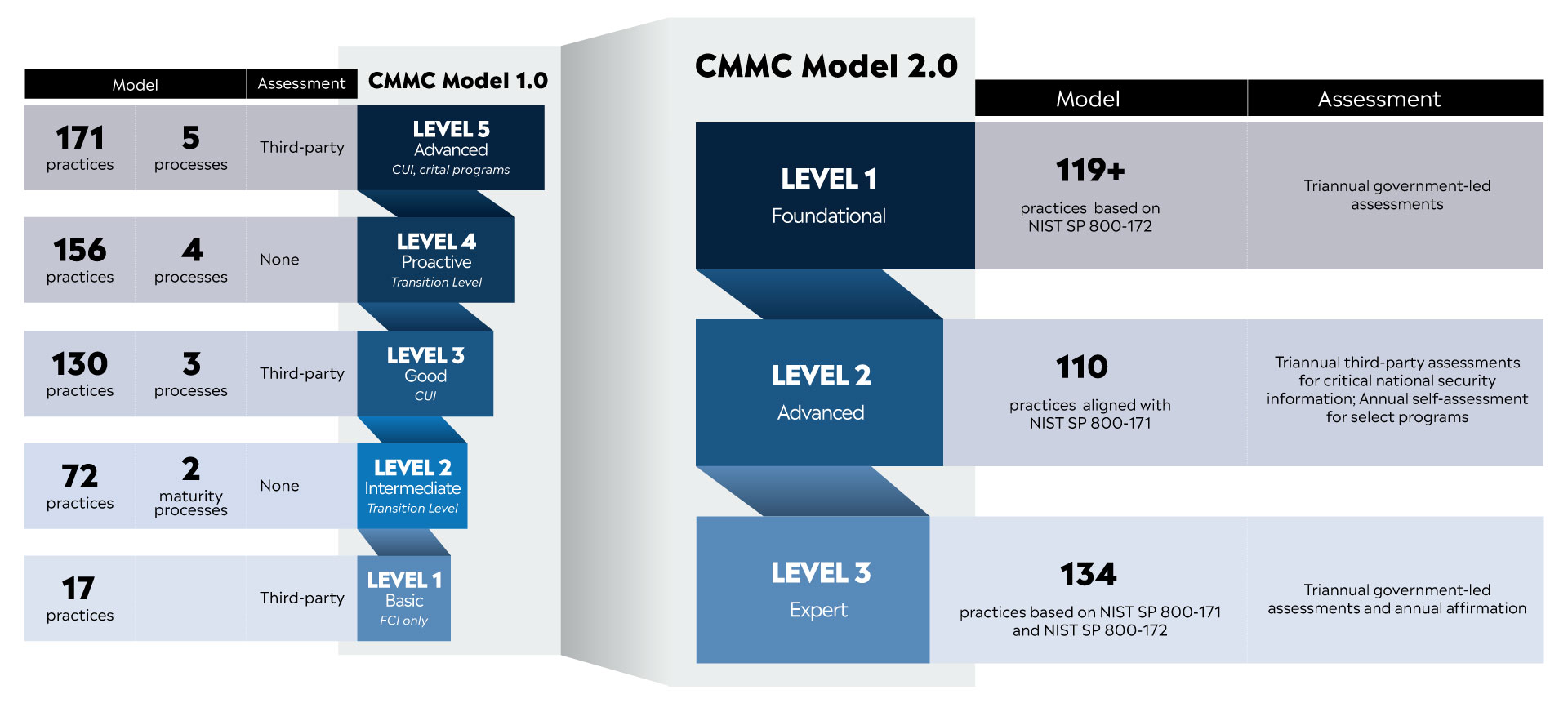
Organizations will be tasked with meeting the NIST 800-171 requirements assigned to each of the three cyber hygiene levels. The forthcoming mandate does away with some process requirements at the lowest level but insists an enterprise “define” upwards of 49 of 110 controls. A cursory look at the three levels shows this could prove a Herculean task for organizations.
- Level 1: Cyber hygiene at this level involves the protection of Federal Contract
Information (FCI) not intended for public disclosure. Although considered “basic” cyber hygiene, military supply chain businesses must address how FCI is handled and stored.
- Level 2: Companies will be required to document the processes used by staff members. It involves achieving cyber hygiene concerning 14 domains and 110 controls.
- Level 3: A contractor’s cybersecurity posture must be so rigorous it can repel the advanced persistent threats presented by enemy nations. Companies must have a regular third-party assessment and maintain a determined posture.
Industry leaders must often prove they achieved the necessary cyber hygiene level to bid on DoD and other federal contracts. Before the federal government crafted the CMMC 2.0 policy, they primarily took a contractor’s word they complied. That all ends now.
2: Plan of Action and Milestones & Waivers
The number of waivers granted is expected to be slimmed down considerably, and a tight policy has reportedly been established. A minimum score for each control must be satisfied, and no waivers will be allowed for the highest weighted controls (i.e., those worth five points).
Cybersecurity experts and national security insiders are hailing this as a win for America’s digital defense. Contractors who previously relied on stop-gap waivers would be well-served to contact a CMMC Third Party Assessment Organization (C3PAO), conduct the necessary due diligence, and harden their defenses.
3: Changes to Self-Assessments
One of the changes from CMMC 1.0 to 2.0 involves what appears to be flexible self-assessments, at least at first blush. The approaching mandate indicates outfits that fall under Level 1 may conduct their assessment and file a score online.
Initially, some Level 2 organizations were going to have a self-assessment option, while others needed to work with a C3PAO, depending on the nature of the FCI or Controlled Unclassified Information (CUI). However, recent reports indicate Level 2 companies will all be mandated to undergo a third-party assessment. As a result, an estimated 80,000 contractors and subcontractors handle FCI and CUI required to meet Level 2 standards. The same holds for contractors within the Level 3 framework.
4: Senior Officials Tasked with Annual Affirmations
One of the top-tier issues CMMC 2.0 seeks to address is accountability. The DoD once fined or suspended companies after determining they failed to meet federal cybersecurity guidelines. Unfortunately, many of the penalties came after a hacker had already absconded sensitive FCI or CUI.
According to a filing in the Federal Register, the newly-conceived cybersecurity regulations allow “annual self-assessment with an annual affirmation by DIB company leadership” in some cases. This means that faulty self-assessments and failure to maintain a Level 1-3 posture may result in the company and senior management personnel suffering consequences. Given the wide-reaching things that could go awry during internal audits, industry leaders would be well-served to onboard a C3PAO.
5: Preparation Timeline Shortened
Early expectations around the CMMC 2.0 rulemaking process were that it would take 9-24 months. Now, contractors and subcontractors have until July before mandates appear in agreements. Industry leaders should start implementing NIST 800-171 controls before the year’s end. When the first quarter of 2023 kicks off, the 300,000 organizations in the defense industrial base will likely overwhelm the availability of C3PAOs, creating a bottleneck.
How to Prepare for CMMC 2.0 Appearing in Contracts
The best preparation strategy may involve scheduling a gap assessment. This cybersecurity analysis deeply delves into systems, best practices, programs, and how FCI and CUI are stored and transmitted. Business leaders receive a report showing network strengths and vulnerabilities. Accompanying recommendations highlight ways to close security gaps and meet the CMMC 2.0 mandate.
Sedulous Consulting Services is an Approved C3PAO Candidate firm. Our dedicated team members can comprehensively conduct a gap assessment and overcome any CMMC 2.0 challenges contractors and subcontractors face. To schedule a gap assessment, contact Sedulous Consulting Services today